Mona Thakkar & Anne Speckhard Militant groups such as the Islamic State (IS) and its…

Islamic State’s global financial networks: Cryptocurrency and European bank transfers fund detained IS women and incarcerated IS fighters in Syria, furthering militant objectives
Mona Thakkar & Anne Speckhard
Five years after the demise of IS’s territorial caliphate in Syria and the subsequent arrival of the IS families in northeastern Syrian camps, IS and its aligned international networks continue to exploit the global financial system marked by their increased use of cryptocurrencies to raise funds for the detainees’ daily needs and securing their escapes via smuggling. This effort has also been largely driven by foreign detainees in Al-Hol and Al-Roj camps running their own crowdfunding initiatives from inside the camps across various social media platforms like Instagram, Facebook, and on encrypted applications like Telegram.
Pro-IS women in the camps, serving as a strategic pool for the group, continue to engage in acts of spreading violence and indoctrinating children with the group’s radical ideology. That they are able to receive substantial funds into the camp via hawala and other illicit transfers is a huge boon to their recruitment efforts as youth born and brought into IS and now detained with mothers, who no longer adhere to the IS ideology, are vulnerable to the women who have the resources to buy them good food, gifts from vendors in the camp and so on in order to seduce them away from their mothers into the terrorist ideology.
Some mothers report their teen girls being recruited in this manner by some female IS acolytes who have a lot of money, with their daughters coming home to their mother’s tent bejeweled with new hair pieces, etc telling their mothers she’s an apostate and must be excommunicated [declared an unbeliever and therefore able to be killed by the group]. Young boys are also lured in the similar way by these women into enhancing their physical strength directing them to perform martial arts, forcing them to act as spies in the camp, enacting violence toward those not adhering to IS ideology, and even to studding some of the boys out to increase the birth rate of the group. Likewise, women in the camps have told the second author about “kill lists” that the IS women make for the event that their “brothers” free them by overrunning the camps so that they can know who are still IS adherents and who must be killed for walking away from IS.
The February report of Operation Inherent Resolve, the ongoing US-led coalition campaign against IS, also reported the threat of IS recruiting and maintaining loyal supporters, and securing their release by transferring them funds—up to $20,000 per month each— through intermediaries in Turkey via the hawala system, cash transfer apps, and increasingly via cryptocurrency. ICSVE’s monitoring likewise reveals a resurgence in the efforts of IS-linked German and Russian networks to mobilize financial resources for smuggling out teenage boys and families out of Al-Hol. However, ambiguity shrouds the fate of these adolescents post- their escape, with questions lingering about how and when they will be handed over to the terror group or infiltrated back to their home countries.
In late February, a pro-IS Russian network of women in Al-Hol on Instagram reignited pleas to smuggle out teenage boys seeking $8000 for each adolescent, in anticipation of Russia’s repatriation of 32 children from Syria in March 2024. Their mothers apparently thought it better to be smuggled out to IS than to be repatriated home into the care of grandparents. Facing constant takedowns on Telegram have compelled these pro-IS Russian networks to shift their fundraising efforts to Instagram, amplifying their reach and visibility among IS supporters and somehow eluding Meta’s takedowns.
The network claimed to have raised $36,000 last year for the escape of 8 children, stating that they “found their way out of the camps to an unknown destination”. Moreover, in the SDF- led security raids in Al-Hol in February that led to the arrest of senior IS militants, IS women claimed that many teenage boys were also separated and taken into ‘rehabilitation centers,’ by SDF adding further impetus to their fundraising efforts. SDF says that rehabilitation is important for pulling children out of extremist thought and clearly separating them is protecting these youth from being smuggled out into the hands of IS. Several escape attempts have also taken place with the SDF claiming that they foiled escape attempts of 2 teenage boys from Al-Hol in March.
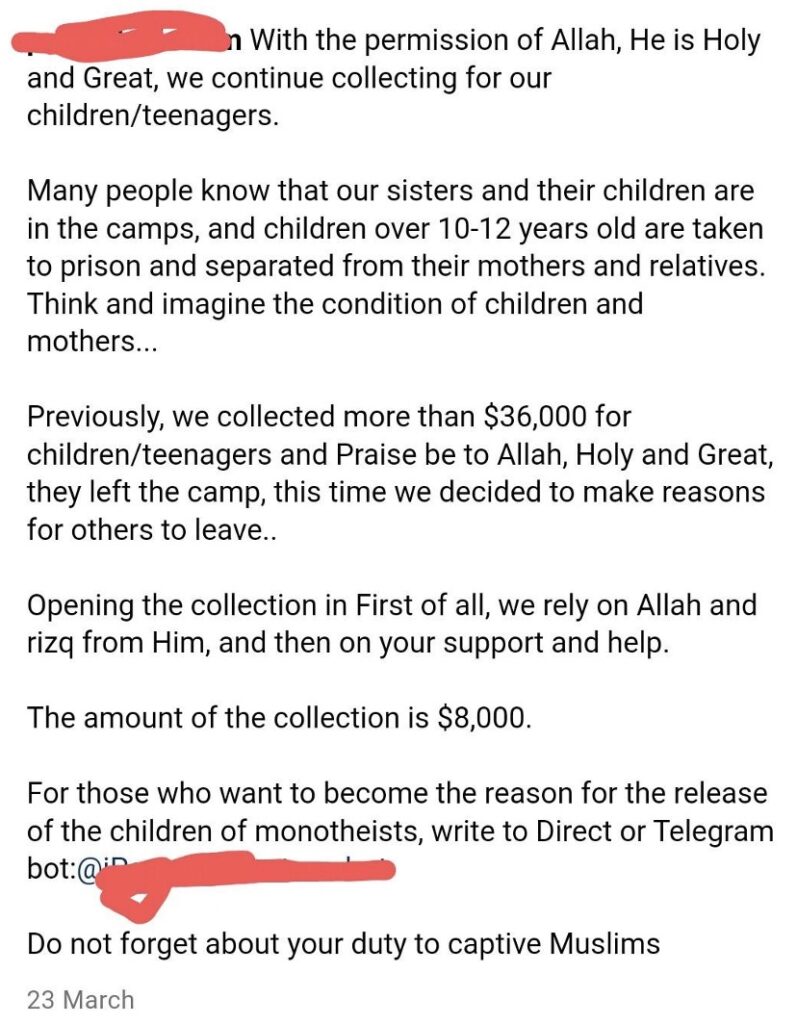
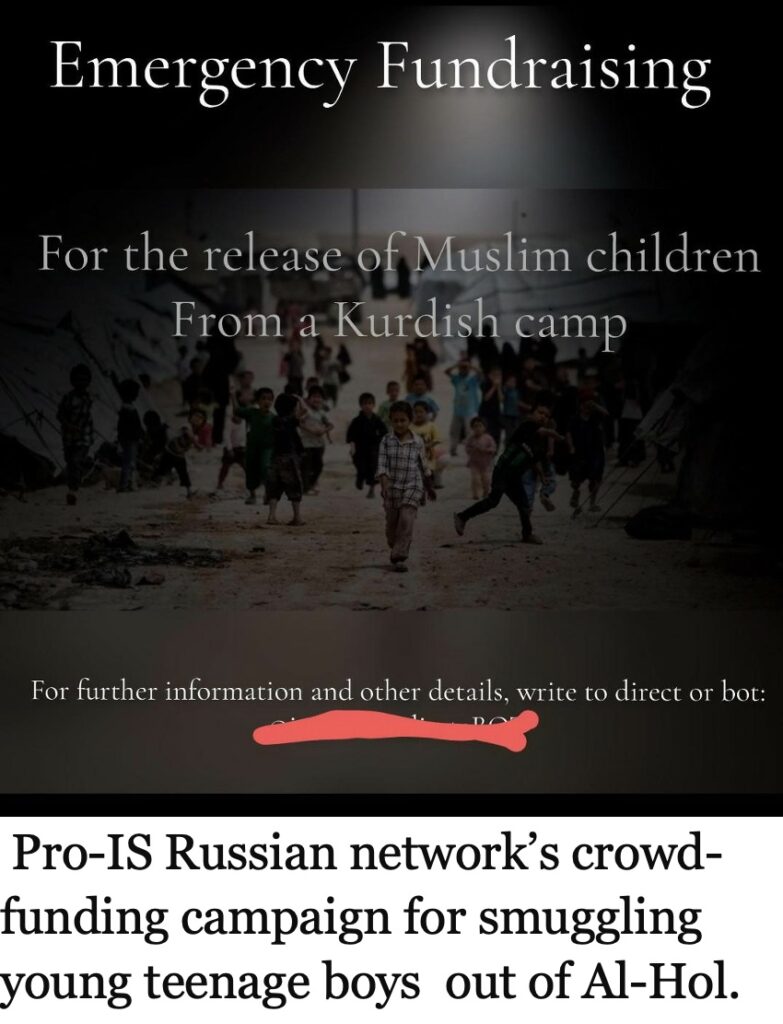
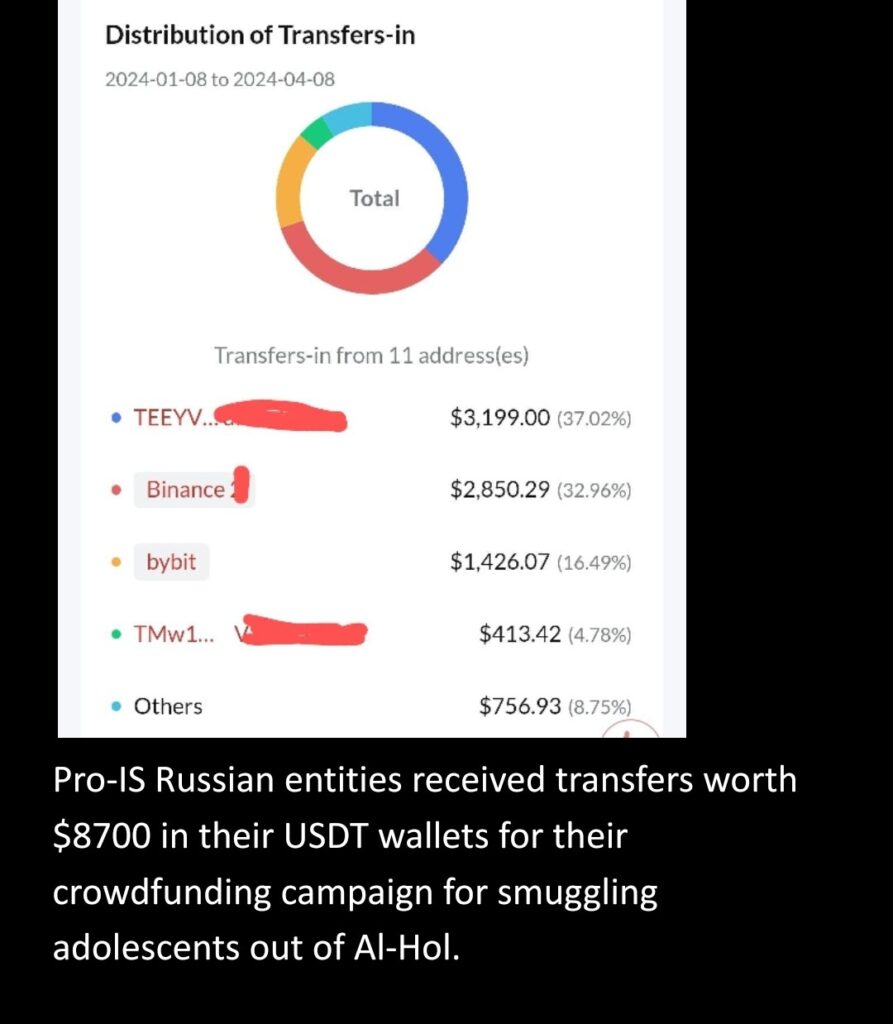
The pro-IS Russian network predominantly secured donations through Russian payment app QIWI and cryptocurrency transfers. A USDT wallet used by this network, monitored by ICSVE, received around $8000 between January and April 2024. Notably, Tether currency remains the preferred choice for IS-linked networks, which also have extensively leveraged traditional banking systems in Europe and Russia for securing detainees’ escapes. This-pro IS Russian crowdfunding campaign employed a beneficiary account of an IS-linked financial facilitator at Dornbirner Sparkasse Bank AG , a small cooperative Austrian bank, alongside accepting transfers through Russian-owned MTS bank — placed under the US sanctions —for freeing detainees.
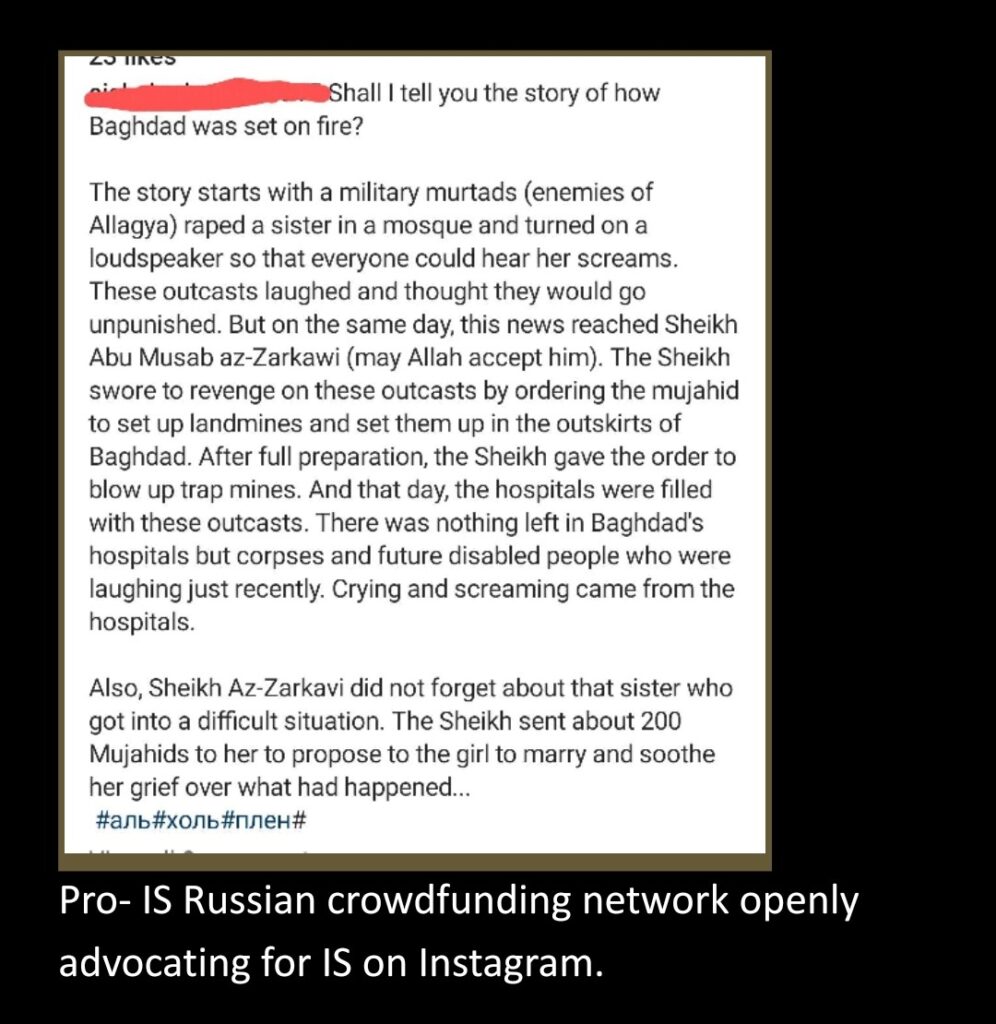
Beyond running donation drives, Russian women amongst all the foreign IS detainees have emerged online to be the most vocal supporters for IS exhibiting extremist tendencies. Social media discourse originating from the camps indicates that the intransigent pro-IS Russian detainees celebrated the attack claimed by the Islamic State central on a Moscow concert venue, which resulted in the death of over 140 individuals decrying “the brutal treatment” of the detained Tajik suspects during their interrogation with the Russian authorities. One woman expressed her sentiments, stating, “Alhamdulillah! If the brothers did it, may Allah grant them even more strength and victories wherever they are? I am elated by such news. If these ‘kafirs’ are harming each other, let their suffering be even more severe!” Other Russian IS sympathizers voiced their support for the group, asserting that the attack on “Russian infidels” was long overdue—a “sin they should pay for, the shedding blood of Muslims in Syria.”

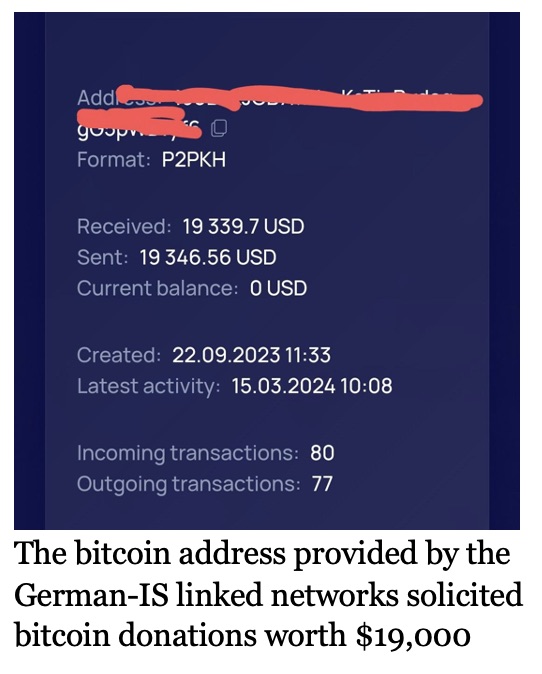
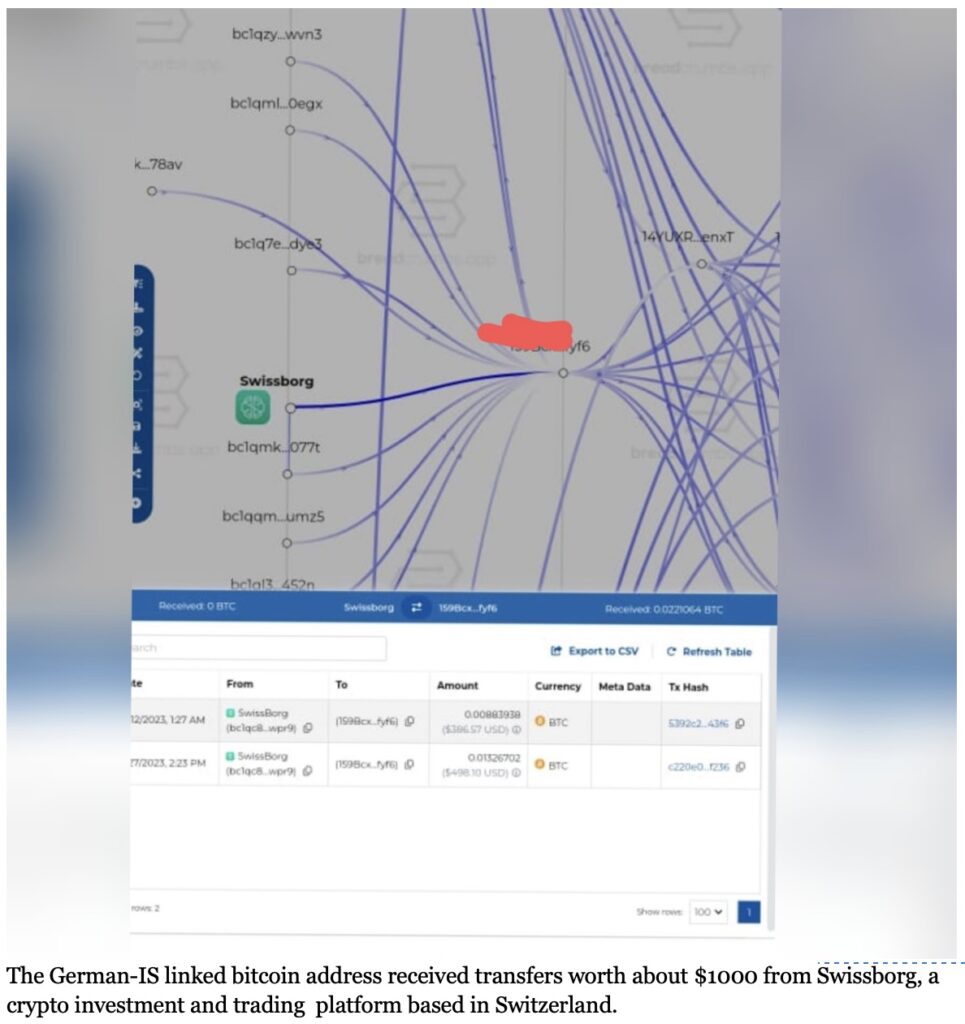
Three German language entities linked to IS, since January 2024, have been covertly collaborating to finance detainees’ under the guise of separate crowdfunding initiatives. They strategically cross-promote their campaigns on Telegram to enhance credibility of their fundraisers. The overarching narrative emphasizes the Islamic obligation of aiding “captives” and “families of mujahedeen,” particularly during Ramadan, when such acts are believed to yield multiplied Islamic rewards. These entities offer flexible money transfer options, including online payment services like PayPal, money transfer services like Western Union, and direct international wire transfers with a minimum limit of €50. A common Bitcoin address shared by all the three German IS-linked networks received a substantial transfer of $20,000 between October 2023 and February 2024, exposing an illicit money trail to Switzerland for the first time. In December 2023, approximately $1000 were sent to German IS-linked Bitcoin addresses from a crypto investment and trading platform Swissborg, based in Lausanne, Switzerland. Moreover, these networks frequently rotate new Tron wallets every 15 days demonstrating the widespread use of tether cryptocurrency for their financial operations.
While IS-linked networks predominantly rely on cryptocurrencies for their fundraising endeavors, the German language IS-linked networks have also increasingly accepted donations through direct bank transfers, providing IBAN details of IS-linked financial intermediaries, unveiling a complex web of money laundering networks across European jurisdictions. To accommodate potential donors with limited knowledge of cryptocurrencies, direct donations through SWIFT transfers are encouraged. Funds earmarked for detainees under the oversight of German-IS networks were diverted to an obscure entity or what looks like a shell company called “Aqua Creative Global” to their Copenhagen-based banking account, Banking Circle SA. Banking Circle SA is a European banking platform specializing in B2B payment solutions, operating across multiple European countries, with its headquarters in Luxembourg. By routing illicit funds purportedly through a shell company based in Denmark, individuals associated with this crowdfunding campaign can evade detection more effectively. This strategy aims at leveraging the legitimacy of the company’s operations and transactions, further complicating efforts to trace and uncover their illicit financial activities. IS-linked German networks also routed suspicious transactions through England with the IS-linked entity receiving transfers on behalf of these networks into the bank account opened with the London based Revolut bank.

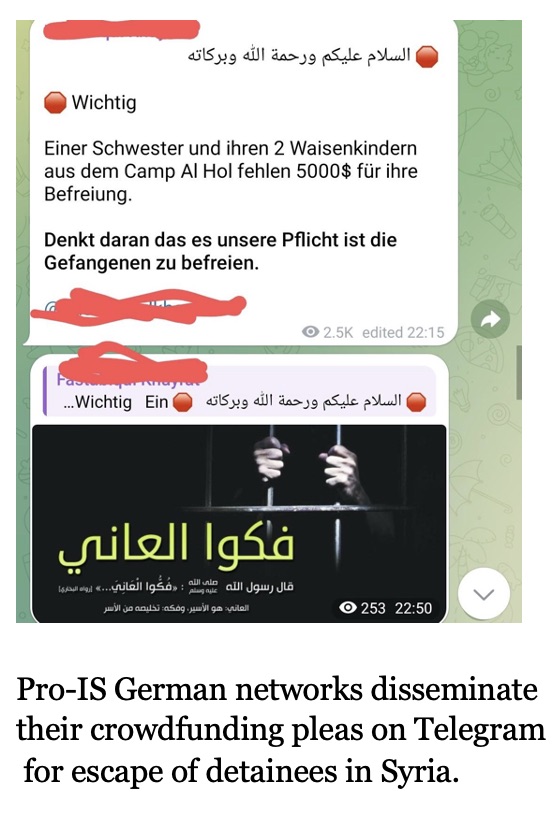
Since 2020, another German network, “Free our Sisters” has been actively soliciting funds to support convicted or arrested IS sympathizers, as well as supporters of other militant groups in Germany. Their fundraising tactics include financially supporting the detainees and their families through selling translated copies of jihadist preacher Sheikh Abu Musa Jibril’s works, known for his influence on Westerners who joined the Syrian conflict, and translating literature from other radical preachers and selling second hand goods like watches, clothes, perfumes etc. In March, the network sought contributions to cover the legal expenses of a woman charged with aiding IS detainees in Syria, with a target of raising €3000. Donations were directed into the recipient’s savings account at Targobank, a local commercial bank based in Dusseldorf, Germany. Despite numerous escape attempts of IS women being thwarted by the Syrian Democratic Forces (SDF), German networks persist in their appeals of smuggling them out of Al-Hol. In February, the German-IS linked entities sought $5000 to secure the escape of a family of four from Al-Hol.


Alongside the German and Russian linked IS networks, the prominent English language IS-linked network, is also running donation drives not only for female detainees but also for incarcerated IS fighters in Kurdish-controlled northeastern Syrian prisons and areas controlled by the Turkish backed Syrian National Army, where they claim sending relief packages is easier as they are “in contact with the brothers”. The administrators of this pro-IS channel have disclosed that the funds could also be directed to meet the specific needs of IS fighters on the frontlines in Syria with whom they maintain direct contact. One of this channel’s supporters, apparently a female detainee, claims nothing has changed in the five years since the Islamic State’s territorial defeat in Baghouz and that the hearts of the foreign fighters remain committed to it.
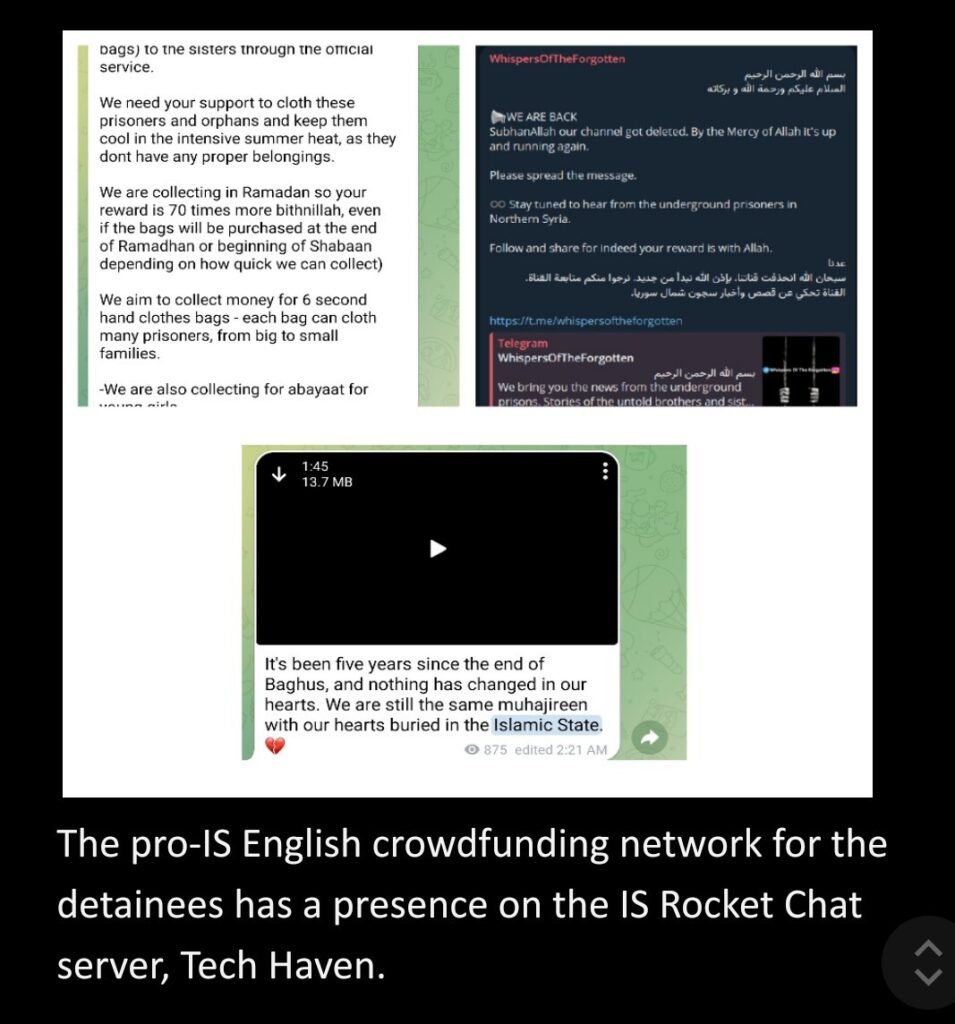
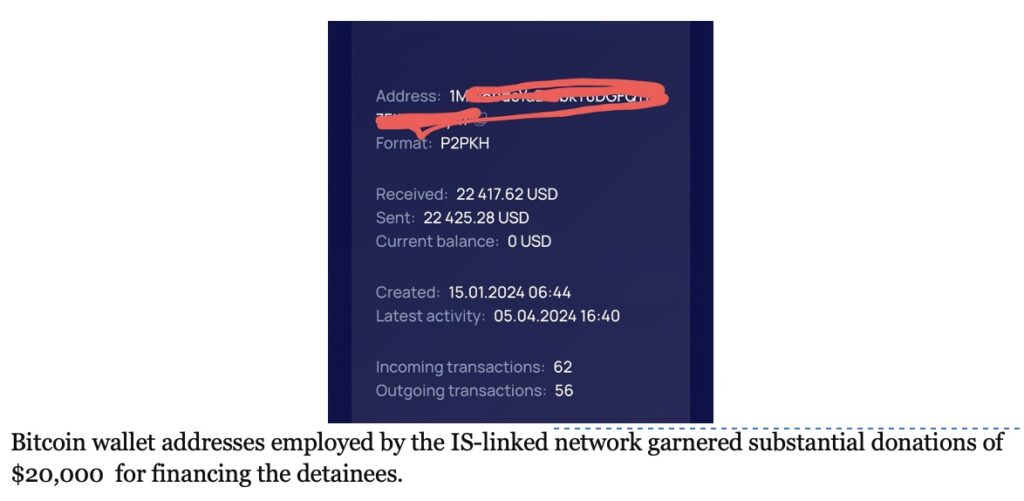
This network also maintains a presence on IS’s rocket chat server, Tech Haven for bolstering its fundraising efforts. The crypto wallet address provided by the networks usually serves as a temporary storage for funds, which are then transferred through multiple wallets before reaching their final destination where they are converted into fiat currency, obscuring the transactional trail. Crowdfunding proceeds, primarily sourced from bitcoin donations, totaled around $22,000 between January and April 2024 for this fundraiser. Moreover, an alternate bitcoin address associated with this pro-IS network has been found channeling funds to an address linked with criminal entities engaged in phishing and impersonation scams. The network advised donors to direct funds to a PayPal merchant address under the “friends and family” option, aiming to bypass transaction fees and blend suspicious transactions with legitimate ones. The administrator of this pro-IS channel also spoke of channeling illicit funds through companies in UAE and other Gulf states.
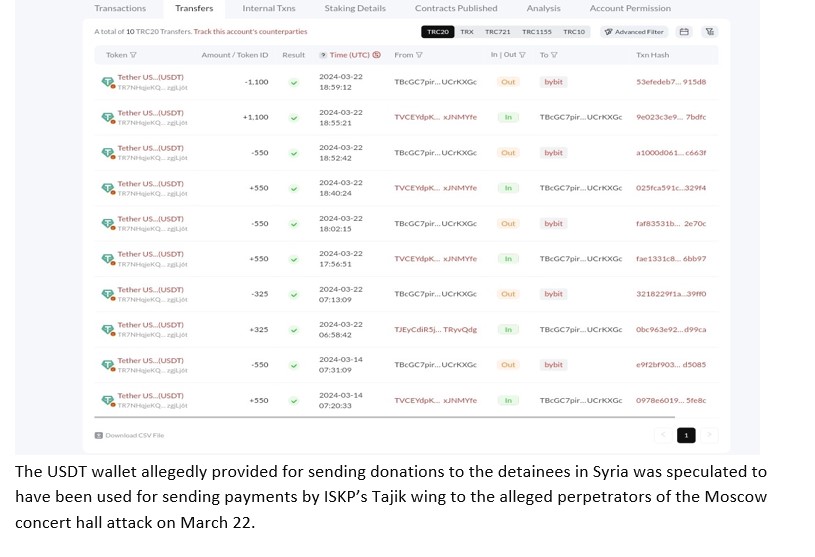
Likewise, the Islamic State in Khorasan province’s Tajik network has been crowdfunding for the female detainees over the past three years. Under the pretext of fundraising to support Tajik IS women, the ISKP Tajik network, this time appears to have diverted funds towards operational and recruitment activities through cryptocurrency transfers. ICSVE discovered that approximately $2700 were transferred in tranches from the USDT address used by ISKP’S Tajik network to Bybit crypto wallet on the same day of the Moscow concert hall attack, March 22nd. Russian and Ukrainian media reports corroborated these findings, suggesting ISKP’ used the USDT wallet to transfer payment to men apprehended in connection with the attack. That ISKP’ ostensibly paid half of the promised amount through USDT transfers to one of the alleged perpetrators further was substantiated when, the detained Tajik national, in his interrogation with the Russian authorities said that he carried out the attack for 5,00000 rubles (roughly $5000) out of which he had received almost half of the amount.
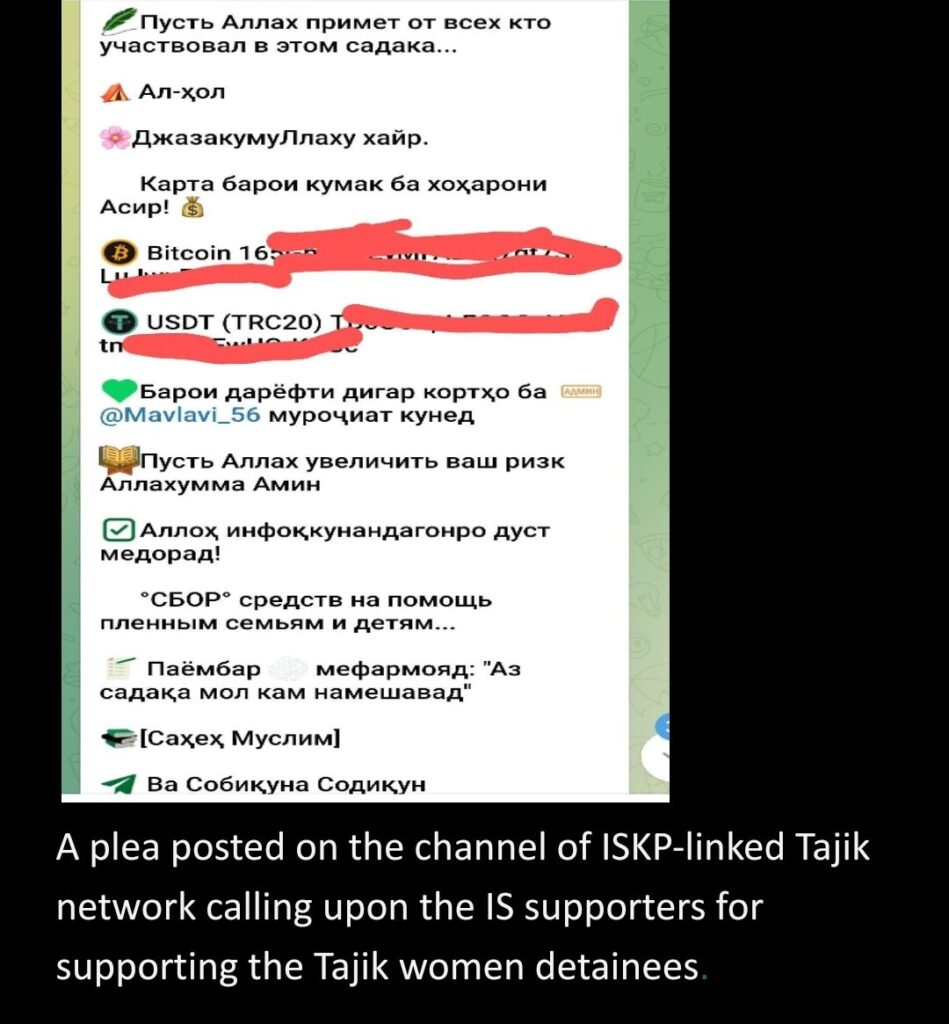
No further transaction activity has been reported post-March 22nd in the USDT wallet used by ISKP’s Tajik network signaling that the crypto address solely created 8 days before the attack, on 14th March, was purportedly used for sending money to the IS fighters who attacked the Moscow concert venue. ISKP’s network was also found converting funds into Syrian pounds for the Tajik IS women routed through the Russian payment service Yandex Money and Russian state-controlled SBER bank. It’s apparent that the Central Asians, particularly ethnic Tajiks who are vulnerable to recruitment for many reasons, have been a primary target for the group’s propaganda and recruitment efforts, with the Tajik contingent playing a significant role in the group’s aggressive fundraising endeavors and perpetrating deadly suicide bombings in Afghanistan and neighboring countries.

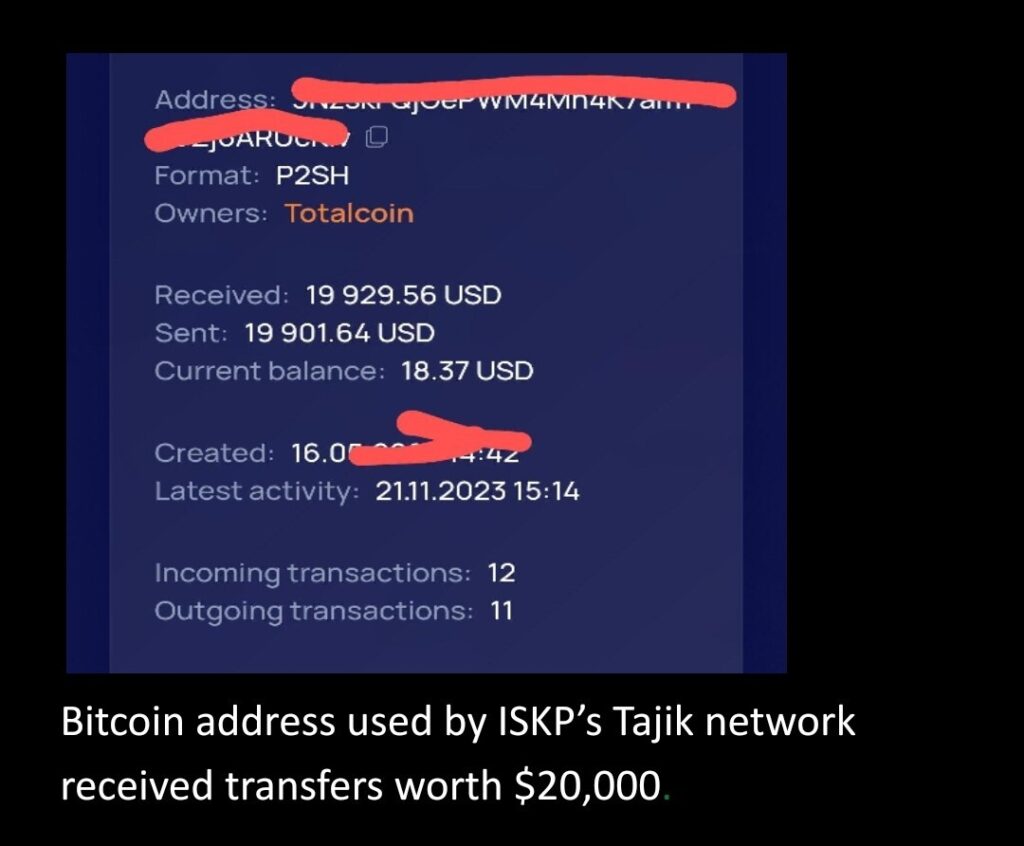
Though ISKP has shown a tendency to employ untraceable privacy oriented crypto currency like Monero, monitoring shows the group has also increasingly channeled funds using bitcoin and tether currencies. Between October and November 2023, a sum of $20,000 was purportedly transacted through a bitcoin address of ISKP via the multi-currency wallet provider Totail.coin. Notably, one of the transfers was sent through centralized virtual exchange Coinex reflecting that mainstream centralized exchanges have been the biggest recipient of illicit cryptocurrency, “taking in just under half of all funds sent from illicit addresses.” Furthermore, upon monitoring the transaction trail, it was revealed that prior recipients of transfers from the aforementioned ISKP-linked bitcoin address had also received funds via the virtual exchange Garantex, which was sanctioned by the US for facilitating financial transactions on dark web markets for criminal actors and terror organizations.
The exploitation of humanitarian causes by militant groups to garner sympathy among Muslims and secure increased funding is a longstanding tactic, not a novel phenomenon. Entities linked to the Islamic State in Pakistan Province (ISPP) previously capitalized on last year’s February earthquakes in Turkey and Idlib, soliciting cryptocurrency donations. The evident exploitation of digital currencies is not limited to the European or Russian-IS linked networks. IS’ has been increasingly using virtual assets like Tether to raise and move money in Africa, owing to its cheaper and faster movement of funds, apart from informal money services like cash couriers forming the lynchpin of its money laundering strategies. Notably, the group and its affiliated networks have thus demonstrated operational security in their cryptocurrency usage, providing followers with guides on secure asset transfers, alongside advocating for decentralized currencies and crypto mixers to obfuscate transaction records.
Thus, these IS-linked financial networks have utilized a multitude of block chains and employed a wide array of techniques like the utilization of common shared addresses, favored wallet providers, temporary addresses, privacy coins, and cash out mechanisms for moving illicit money as a part of their convoluted money laundering system. With crypto transfers, nearly all of the monitored networks soliciting donations for IS women exhorted prospective donors to send money to various IS-linked intermediaries in Istanbul through Western Union, reinforcing Turkey’s role as a logistic base for the group’s illicit financial flows, alongside serving for years as a hub to transfer IS fighters and otherwise support IS. One jihadist fighter from the EU who spoke to the second author confirmed that during the IS Caliphate any money that entered Turkey via the hawala system was essentially available to those in Syria. Likewise, another IS fighter told the second author about running a hawala system in Turkey, with the full knowledge of Turkish police and other intelligence authorities, to finance the IS fighters in Syria during its territorial Caliphate.
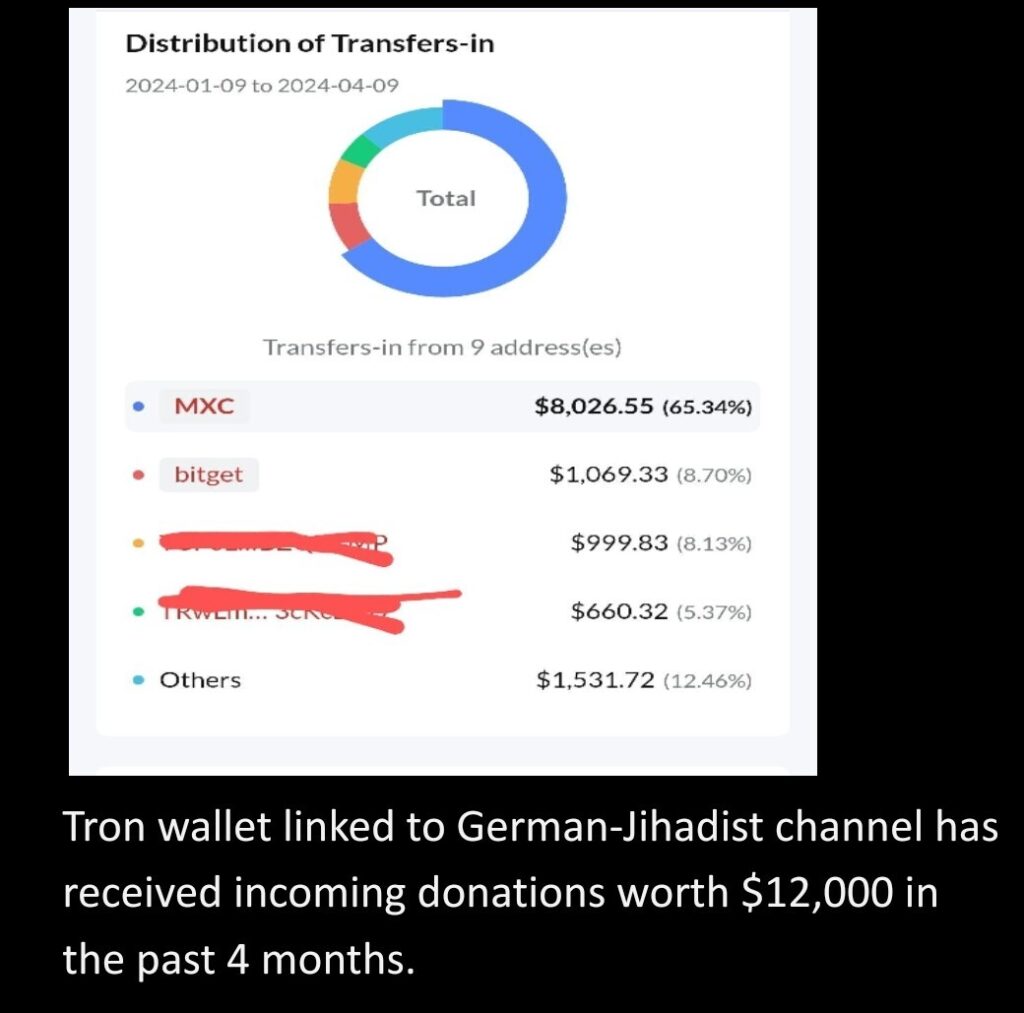
In Syria’s northwestern province of Idlib, controlled by jihadist group Hayat Tahrir al-Sham, foreign fighters affiliated with various jihadist outfits are also gradually turning to running crowdfunding campaigns seeking cryptocurrency donations. A troubling development emerges as a German jihadist who claims to be in Syria since 2013, continues to document his firsthand experiences from the frontlines in Idlib on his Telegram channel. While advocating for humanitarian aid to the war-torn populations in Gaza and Idlib, the jihadist diverted funds to support his own family and ostensibly for buying weaponry for the militant group he belongs to. Notably, the Tron wallet address shared by the militant for accepting transfers received $12,000 between January and April 2024, signaling a significant flow of funds being diverted for militant operations.

In summary, this study sheds light on the persistent financial strategies employed by IS and it’s linked or affiliated international networks which include the exploitation of various financial mechanisms, such as cryptocurrencies and European banking systems, to raise funds for detainees and for fulfilling IS’s militant goals. These findings underscore the necessity for enhanced international monitoring and robust collaboration between various countries and UN bodies to disrupt the financial infrastructure of terrorist organizations like IS and other militant groups, which is vital for mitigating the ongoing threat posed by the group and its networks to global security and stability. This is particularly salient when it comes to the illicit funds received into the camps by female IS loyalists who are using them for grooming children born and brought up in these sprawling camps to become future wives, fathers and jihadist fighters for IS’—fighters our troops may be facing down in the future.
About the authors:
Mona Thakkar is a research fellow at the International Centre for the Study of Violent Extremism, where she focuses on monitoring militant jihadist groups and their financial networks. Follow Mona on X: @ t16_mona
Anne Speckhard, Ph.D., is Director of the International Center for the Study of Violent Extremism (ICSVE) and serves as an Adjunct Associate Professor of Psychiatry at Georgetown University School of Medicine. She has interviewed over 700 terrorists, their family members and supporters in various parts of the world including in Western Europe, the Balkans, Central Asia, the Former Soviet Union and the Middle East. In the past three years, she has interviewed ISIS (n=239) defectors, returnees and prisoners as well as al Shabaab cadres (n=16) and their family members (n=25) as well as ideologues (n=2), studying their trajectories into and out of terrorism, their experiences inside ISIS (and al Shabaab), as well as developing the Breaking the ISIS Brand Counter Narrative Project materials from these interviews which includes over 175 short counter narrative videos of terrorists denouncing their groups as un-Islamic, corrupt and brutal which have been used in over 125 Facebook campaigns globally.
She has also been training key stakeholders in law enforcement, intelligence, educators, and other countering violent extremism professionals on the use of counter-narrative messaging materials produced by ICSVE both locally and internationally as well as studying the use of children as violent actors by groups such as ISIS and consulting with governments on issues of repatriation and rehabilitation. In 2007, she was responsible for designing the psychological and Islamic challenge aspects of the Detainee Rehabilitation Program in Iraq to be applied to 20,000 + detainees and 800 juveniles. She is a sought after counterterrorism expert and has consulted to NATO, OSCE, the EU Commission and EU Parliament, European and other foreign governments and to the U.S. Senate & House, Departments of State, Defense, Justice, Homeland Security, Health & Human Services, CIA, and FBI and appeared on CNN, BBC, NPR, Fox News, MSNBC, CTV, and in Time, The New York Times, The Washington Post, London Times and many other publications. She regularly speaks and publishes on the topics of the psychology of radicalization and terrorism and is the author of several books, including Talking to Terrorists, Bride of ISIS, Undercover Jihadi and ISIS Defectors: Inside Stories of the Terrorist Caliphate. Follow Anne Speckahard on X: @AnneSpeckhard



